Latest Phishing Trends (Oct 2025)
We have identified multiple phishing attempts against schools and charities in the UK and wanted to share the latest trends to keep as many people informed as possible.
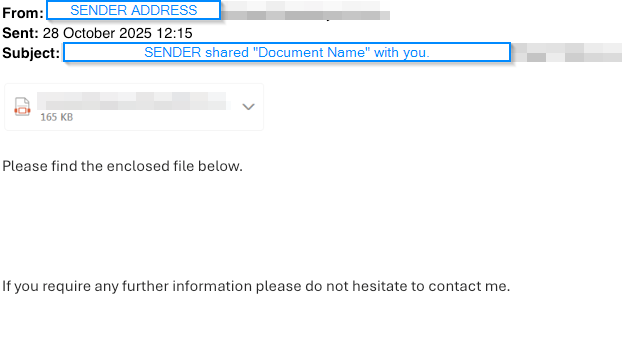
The latest trend are emails from known contacts containing questionable links, titled similarly to ‘John Smith has shared a document with you’. With John Smith being the name of your known contact. This relatively new form of phishing attack rapidly emails all their known recipients and senders in their mailbox pretending to share an important document with you.
This link resembles a sharing link that you may receive from someone when they share a document from Microsoft OneDrive / SharePoint or Google Drive. Whereas in this case it is an image of an attachment, which sends you to a malicious website displaying a sign-in page similar to Microsoft / Google where you may inadvertently share your account details with the attacker and they take your authenticated cookie from your web browser to circumvent Multi-Factor Authentication (MFA/2FA).
In short, awarding the attacker with your email account details and the MFA keys to your account for them to steal your data and repeat the attack with your contacts.
Below is an example of such an email.
Ask yourself:
Do not reply
Do not reply asking the user if this email is legitimate. In a lot of cases the attacker will set up automatic replies stating that it is a safe mail when it is not. The real user will not receive your email as the attacker will hide attempts from others to inform them of the issue. If you know the sender the best thing you can do is to call them and let them know over the phone or in person. This way your communication cannot be intercepted.
I hope this article has proved helpful and can be used to keep you and your users informed of the latest email threats targeting UK organisations. If you believe that you have already been hacked and require further assistance, you’re welcome to reach out to our team and we will endeavour to resecure your IT.
Recommendations
- User Awareness Training – Ensure that your staff are aware of the latest security trends, whether by online training services or in-person training sessions.
- Advanced Email Protection – Introducing an email security solution that detects and prevents incoming threats to your emails.
- Backup & Disaster Recovery – Apply a backup solution for your communications & data and documenting a disaster recovery process or business continuity plan to quickly recover from an attack.
We can supply all of the above, if you are interested in hearing how we can implement one of these solutions into your IT, you’re welcome to reach out to me.
Get in touch with our Experts
Do you think that you have been hacked? Give us a call to discuss how we can resecure your IT.